-
use different monoalphabetic substitution functions
depending on plaintext character position
- shift by a keyword
key: beauty plaintext: aaaaaabbbbbbabcabc ciphertext: beautycfbvuzbfcuua
-
characters at position 6i+1 are shifted by 1 ('b' - 'a')
characters at position 6i+2 are shifted by 4 ('e' - 'a')
...Or, plaintext and key characters can be XORed to yield the ciphertext.
- rotor machines using multiple rotors:
-
each rotor implements a permuted alphabet cipher;
an output from one rotor is the input to the next rotor;
rotors are rotated like clock hands.ex) German Enigma during World War II with 5 rotors
- One-time pads if every plaintext character is transformed using a different substitution function, and the substitution functions are independent from each other.
Transposition
- Simple columnar transposition cipher
plaintext: thisistheplaintext thisis thepla intext ciphertext: tti hhn iet spe ilx sat
- Simple columnar transposition cipher + permuted columns
plaintext: thisistheplaintext key: beauty (231546) thisis thepla intext ciphertext: iet tti hhn ilx spe sat
- multiple stages of transpositions with different column sizes
plaintext: thisistheplaintext key 1: beauty (231546) thisis thepla intext key 2: thank (52143) iettt ihhni lxspe sat## ciphertext: thst ehxa tie# tnp# iils
-
Lessons from simple ciphers
- Repeating monoalphabetic substitutions by permuted alphabet doesn't
increase cryptographic strength at all.
- Multi-stage transposition helps.
- Combining substitution and transposition results in
even stronger ciphers.
-
ex) German ADFGVX cipher during World War I
- Cryptographic strength of most simple ciphers depends on
the secrecy of algorithms and key parameters both.
- New ciphers are devised to resist known attacks.
- Confusion and Diffusion by C. E. Shannon
- confusion: obscuring the relationship between the plaintext and the ciphertext.
- diffusion: spreading the information from the plaintext over the entire ciphertext.
- Avalanche effects: a small change in either the plaintext
or the key produces a change in many bits of the ciphertext
- Repetition of nonlinear transformations ( --> product cipher)
- Cryptographic strength should depend on the secrecy of the key,
not the secrecy of algorithms.
- Shorter keys are better unless it weakens the cryptographic strength seriously.
- Algorithms should yield efficient implementation in hardware and/or software.
Characteristics
DES algorithm
DES design considerations
Attacks on DES (Is DES safe?)
This attack assumes one known pair of plaintext and ciphertext;
the attack is still possible without known plaintext but with some
known pattern of plaintext (such as ASCII) and it may take longer.
Solution: 3DES (or DES-EDE) using two keys --
EK1(DK2(EK1(P)))
DES applications
UNIX password encryption repeats DES 25 times
with modified expansion permutation by a random 12-bit value,
thus making hardware key search (with commercial DES chip) impossible.
PIN-based ATM
DTi: date and time
Ri = EDEK1,K2(EDEK1,K2(DTi) XOR Vi)
RC5 (Rivest Cipher 5)
Blowfish
SEED
Block Ciphers
(Chapter 7 of
Handbook of Applied Cryptography, in PostScript)
Advanced Encryption Standard (AES) Development Effort
Round 2 [8/1999-5/2000] Candidate Algorithms:
MARS, RC6, RIJNDAEL, SERPENT, TWOFISH
2. Data Encryption Standard (DES)
History
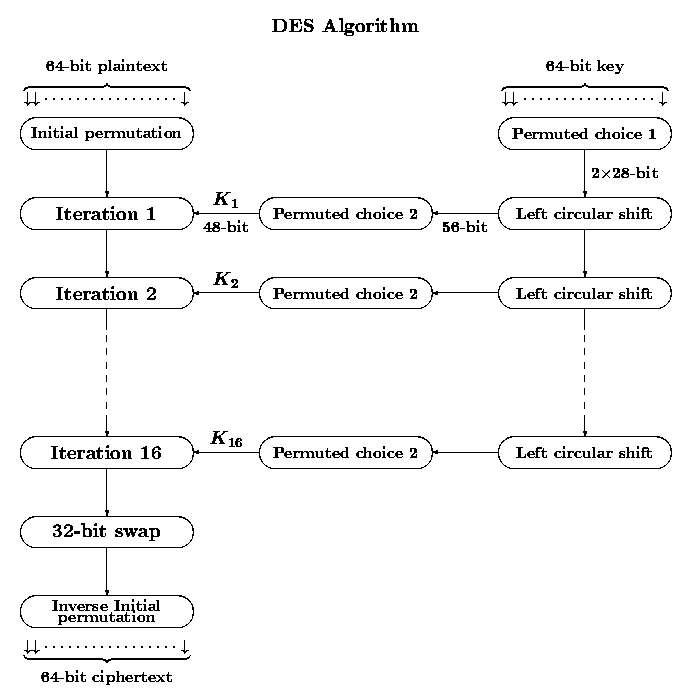
Initial permutation
58, 50, 42, 34, 26, 18, 10, 2,
60, 52, 44, 36, 28, 20, 12, 4,
62, 54, 46, 38, 30, 22, 14, 6,
64, 56, 48, 40, 32, 24, 16, 8,
57, 49, 41, 33, 25, 17, 9, 1,
59, 51, 43, 35, 27, 19, 11, 3,
61, 53, 45, 37, 29, 21, 13, 5,
63, 55, 47, 39, 31, 23, 15, 7
Inverse initial permutation
40, 8, 48, 16, 56, 24, 64, 32,
39, 7, 47, 15, 55, 23, 63, 31,
38, 6, 46, 14, 54, 22, 62, 30,
37, 5, 45, 13, 53, 21, 61, 29,
36, 4, 44, 12, 52, 20, 60, 28,
35, 3, 43, 11, 51, 19, 59, 27,
34, 2, 42, 10, 50, 18, 58, 26,
33, 1, 41, 9, 49, 17, 57, 25
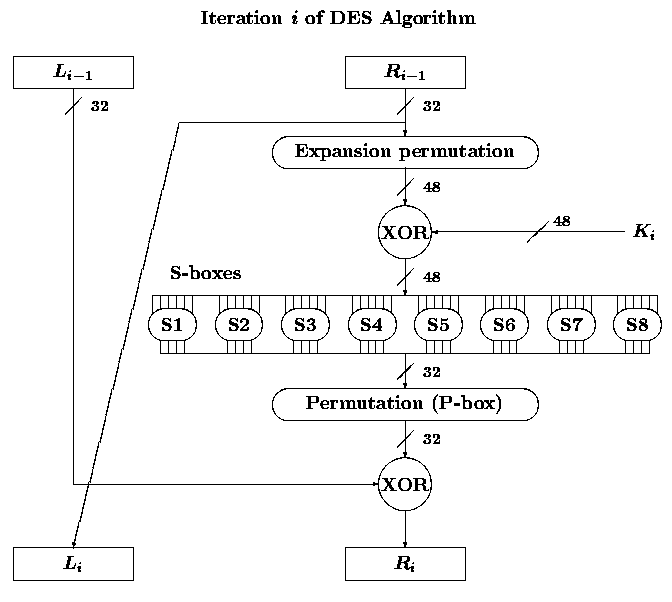
Expansion permutation
32, 1, 2, 3, 4, 5,
4, 5, 6, 7, 8, 9,
8, 9, 10, 11, 12, 13,
12, 13, 14, 15, 16, 17,
16, 17, 18, 19, 20, 21,
20, 21, 22, 23, 24, 25,
24, 25, 26, 27, 28, 29,
28, 29, 30, 31, 32, 1
Permuted choice 1
57, 49, 41, 33, 25, 17, 9,
1, 58, 50, 42, 34, 26, 18,
10, 2, 59, 51, 43, 35, 27,
19, 11, 3, 60, 52, 44, 36,
63, 55, 47, 39, 31, 23, 15,
7, 62, 54, 46, 38, 30, 22,
14, 6, 61, 53, 45, 37, 29,
21, 13, 5, 28, 20, 12, 4
Left rotation table
1,2,4,6,8,10,12,14,15,17,19,21,23,25,27,28
Permuted choice 2
14, 17, 11, 24, 1, 5,
3, 28, 15, 6, 21, 10,
23, 19, 12, 4, 26, 8,
16, 7, 27, 20, 13, 2,
41, 52, 31, 37, 47, 55,
30, 40, 51, 45, 33, 48,
44, 49, 39, 56, 34, 53,
46, 42, 50, 36, 29, 32
S-boxes
/* S1 */
14, 4, 13, 1, 2, 15, 11, 8, 3, 10, 6, 12, 5, 9, 0, 7,
0, 15, 7, 4, 14, 2, 13, 1, 10, 6, 12, 11, 9, 5, 3, 8,
4, 1, 14, 8, 13, 6, 2, 11, 15, 12, 9, 7, 3, 10, 5, 0,
15, 12, 8, 2, 4, 9, 1, 7, 5, 11, 3, 14, 10, 0, 6, 13,
/* S2 */
15, 1, 8, 14, 6, 11, 3, 4, 9, 7, 2, 13, 12, 0, 5, 10,
3, 13, 4, 7, 15, 2, 8, 14, 12, 0, 1, 10, 6, 9, 11, 5,
0, 14, 7, 11, 10, 4, 13, 1, 5, 8, 12, 6, 9, 3, 2, 15,
13, 8, 10, 1, 3, 15, 4, 2, 11, 6, 7, 12, 0, 5, 14, 9,
/* S3 */
10, 0, 9, 14, 6, 3, 15, 5, 1, 13, 12, 7, 11, 4, 2, 8,
13, 7, 0, 9, 3, 4, 6, 10, 2, 8, 5, 14, 12, 11, 15, 1,
13, 6, 4, 9, 8, 15, 3, 0, 11, 1, 2, 12, 5, 10, 14, 7,
1, 10, 13, 0, 6, 9, 8, 7, 4, 15, 14, 3, 11, 5, 2, 12,
/* S4 */
7, 13, 14, 3, 0, 6, 9, 10, 1, 2, 8, 5, 11, 12, 4, 15,
13, 8, 11, 5, 6, 15, 0, 3, 4, 7, 2, 12, 1, 10, 14, 9,
10, 6, 9, 0, 12, 11, 7, 13, 15, 1, 3, 14, 5, 2, 8, 4,
3, 15, 0, 6, 10, 1, 13, 8, 9, 4, 5, 11, 12, 7, 2, 14,
/* S5 */
2, 12, 4, 1, 7, 10, 11, 6, 8, 5, 3, 15, 13, 0, 14, 9,
14, 11, 2, 12, 4, 7, 13, 1, 5, 0, 15, 10, 3, 9, 8, 6,
4, 2, 1, 11, 10, 13, 7, 8, 15, 9, 12, 5, 6, 3, 0, 14,
11, 8, 12, 7, 1, 14, 2, 13, 6, 15, 0, 9, 10, 4, 5, 3,
/* S6 */
12, 1, 10, 15, 9, 2, 6, 8, 0, 13, 3, 4, 14, 7, 5, 11,
10, 15, 4, 2, 7, 12, 9, 5, 6, 1, 13, 14, 0, 11, 3, 8,
9, 14, 15, 5, 2, 8, 12, 3, 7, 0, 4, 10, 1, 13, 11, 6,
4, 3, 2, 12, 9, 5, 15, 10, 11, 14, 1, 7, 6, 0, 8, 13,
/* S7 */
4, 11, 2, 14, 15, 0, 8, 13, 3, 12, 9, 7, 5, 10, 6, 1,
13, 0, 11, 7, 4, 9, 1, 10, 14, 3, 5, 12, 2, 15, 8, 6,
1, 4, 11, 13, 12, 3, 7, 14, 10, 15, 6, 8, 0, 5, 9, 2,
6, 11, 13, 8, 1, 4, 10, 7, 9, 5, 0, 15, 14, 2, 3, 12,
/* S8 */
13, 2, 8, 4, 6, 15, 11, 1, 10, 9, 3, 14, 5, 0, 12, 7,
1, 15, 13, 8, 10, 3, 7, 4, 12, 5, 6, 11, 0, 14, 9, 2,
7, 11, 4, 1, 9, 12, 14, 2, 0, 6, 10, 13, 15, 3, 5, 8,
2, 1, 14, 7, 4, 10, 8, 13, 15, 12, 9, 0, 3, 5, 6, 11
32-bit permutation function P used on the output of the S-boxes
16, 7, 20, 21,
29, 12, 28, 17,
1, 15, 23, 26,
5, 18, 31, 10,
2, 8, 24, 14,
32, 27, 3, 9,
19, 13, 30, 6,
22, 11, 4, 25
i-th round encryption process
Li = Ri-1
(17 - i)-th round decryption process
Ri = Li-1 XOR
f(Ri-1, Ki)
Ri-1 = Li
Li-1 = Ri XOR
f(Ri-1, Ki)
= Ri XOR
f(Li, Ki)
$20,000,000 machine can exhaust the key space in one day.
$1,000,000 machine can exhaust the key space in eight days.
$1,000,000 machine can exhaust the key space in 3.5 hours.
(see des_key_search.ps)
Vi: seed value
Ri: generated pseudorandom number
K1, K2: DES-EDE keys
Vi+1 = EDEK1,K2(EDEK1,K2(DTi) XOR Ri)
3. Other block ciphers
International Data Encryption Algorithm (IDEA)
40-bit key version of these ciphers are exportable
(In alphabetical order, with links to each submitter's web page)
Algorithm Name
Submitter Name(s)
CAST-256
Entrust Technologies, Inc. (represented by Carlisle Adams)
CRYPTON
Future Systems, Inc. (represented by Chae Hoon Lim)
DEAL
Richard Outerbridge, Lars Knudsen
DFC
CNRS - Centre National pour la Recherche Scientifique - Ecole Normale Superieure (represented by Serge Vaudenay)
E2
NTT - Nippon Telegraph and Telephone Corporation (represented by Masayuki Kanda)
FROG
TecApro Internacional S.A. (represented by Dianelos Georgoudis)
HPC
Rich Schroeppel
LOKI97
Lawrie Brown, Josef Pieprzyk, Jennifer Seberry
MAGENTA
Deutsche Telekom AG (represented by Dr. Klaus Huber)
MARS
IBM (represented by Nevenko Zunic)
RC6TM
RSA Laboratories (represented by Burt Kaliski)
RIJNDAEL
Joan Daemen, Vincent Rijmen
SAFER+
Cylink Corporation (represented by Charles Williams)
SERPENT
Ross Anderson, Eli Biham, Lars Knudsen
TWOFISH
Bruce Schneier, John Kelsey, Doug Whiting, David Wagner, Chris Hall, Niels Ferguson