Lecture 9. E-mail Security and PGP
9.1 전자우편 보안의 필요성과 목표
9.2 메시지 암호화 알고리즘과 디지털 서명
9.3 PGP (Pretty Good Privacy) 개요
9.4 UNIX용 PGP 6.5.1 사용법
9.5 기타 전자 우편 보안 관련 사항들
9.1 전자우편 보안의 필요성과 목표
전자우편 보안 목표
-
기밀성 (Message Privacy, Confidentiality, or Secrecy)
제 3자가 메시지를 가로채더라도 그 내용을 알아볼 수 없게 함
-
인증 (Originator Authentication)
발신자 이외의 사람이 메시지를 위조하는 것을 방지함
-
무결성 (Message Integrity)
발신자 이외의 사람이 메시지를 변조하는 것을 방지함
-
발신자 부인 방지 (Originator Nonrepudiation)
메시지 발신자가 메시지를 보낸 사실을 부인하는 것을 방지함
-
기타
발신 사실 증명, 수신자 부인 방지, 전송 경로 보안, 익명성 보장
일반 우편물과의 비교
-
기밀성 : 봉인 (취약함)
-
인증 : 서명
-
무결성 : 서명 + 물리적 검사
-
발신자 부인 방지 : 서명
-
기타
-
발신 사실 증명 : 등기
-
수신자 부인 방지 : 등기
-
전송 경로 보안 : 발신자 주소에 익명 또는 가명
-
익명성 보장 : 익명 또는 가명 우편물
전자우편의 보안 취약성
-
기밀성에 대한 공격:
-
수신자 권한 취득: 수신자 ID와 password의 도용
-
수신측 root 권한 취득: 시스템 해킹 또는 시스템 관리자
-
/usr/mail/recipient-id: 수신자 우편함 파일을 편집
-
$HOME/mbox: 이미 읽은 메시지들을 저장해 두는 파일
-
/usr/spool/mqueue/xxxxxxxx: 발신되는 우편이 순간적으로 저장되는
파일
-
패킷 스니핑 (Packet Sniffing): 발신자측 LAN, 수신자측 LAN, 또는 중간 매개
Gateway
-
트로이 목마
-
인증에 대한 공격:
-
발신자 권한 취득: 발신자 ID와 password의 도용
-
발신측 root 권한 취득: 발신자 password를 변경한 후, 발신자 ID로 로그-인,
메시지 위조 전송, 다음에 원래 패스워드 복원
-
우편 메시지 패킷 조작
-
무결성에 대한 공격:
-
발신자 부인 방지에 대한 공격:
발신자의 부인 (발신자가 패스워드 노출 가능성을 암시)
기밀성에 대한 공격 사례
수신자의 host에서 root 권한을 취득한 후 /usr/mail 또는 /var/mail 디렉토리에
각 사용자의 ID와 같은 이름의 전자 우편 파일을 읽는다
cs:/usr/mail> whoami
root
cs:/usr/mail> ls -l
-rw-rw---- 1 ahs mail 0 11월 5일 10:13 ahs
.................
-rw-rw---- 1 rhee mail 44455 11월 14일 14:28 rhee
-rw-rw---- 1 root mail 32136 11월 9일 17:29 root
-rw-rw---- 1 route mail 14340 11월 13일 11:08 route
.................
cs:/usr/mail> cat rhee
Message-Id: <199610....19.UAA16995@audio20.prognet.com>
To: rhee@cs.sookmyung.ac.kr
From: RealAudio Talking E-mail
Subject: Hear Near-CD Quality Audio Over Standard Modems
Dear RealAudio Customer,
Since you downloaded our free RealAudio Player a while back,
you have heard some pretty amazing things on the Web.
Now you can hear even more with RealAudio Player Plus,
http://www.realaudio.com/bplus/index.html
.................
Rob Glaser Bruce Jacobsen
Progressive Networks Progressive Networks
Chairman & CEO, President & COO,
cs:/home/rhee 4 > telnet soback.kornet.nm.kr 25
......................
220-soback.kornet.nm.kr Sendmail 8.6.12h2/8.6.9
ready at Thu, 14 Nov 1996 19:36:32 +0900
220 ESMTP spoken here
HELO soback.kornet.nm.kr
250 soback.kornet.nm.kr Hello cs.sookmyung.ac.kr
[203.252.195.1], pleased to meet you
MAIL FROM: yskim@top.bluehouse.go.kr
250 yskim@top.bluehouse.go.kr... Sender ok
RCPT TO:rhee@egret.sookmyung.ac.kr
250 rhee@egret.sookmyung.ac.kr... Recipient ok
DATA
354 Enter mail, end with "." on a line by itself
This is a forged letter.
Bye.
.
250 TAA17746 Message accepted for delivery
[/u/rhee] Mail
"/usr/spool/mail/rhee": 1 message 1 new
>N 1 yskim@top.bluehouse.go.kr Thu Nov 14 10:29 11/637
& 1
Message 1:
From daemon Thu Nov 14 10:29:42 1996
From: yskim@top.bluehouse.go.kr
Date: Thu, 14 Nov 1996 19:37:48 +0900
Apparently-To: rhee@egret.sookmyung.ac.kr
This is a forged letter.
Bye.
9.2 메시지 암호화 알고리즘과 디지털 서명
일반적으로 기밀성은 메시지의 암호화를 통해, 인증과 무결성 검사는 디지털
서명을 이용하여 구현한다.
암호화 알고리즘
-
대칭 암호화 알고리즘 (symmetric encryption)
-
암호화 및 해독에 동일한 암호키 (비밀키) 사용
-
처리 속도가 빠름
-
암호키 전달 및 관리의 문제가 있음
-
DES, IDEA, CAST, 3DES, RC2, RC5
-
비대칭 암호화 알고리즘 (asymmetric encryption)
-
공개키와 개인키로 불리우는 한 쌍의 암호키가 사용됨
-
암호화에는 공개키, 해독에는 개인키를 사용하며 그 역할을 바꿀 수 있음
-
두 개의 암호키는 수학적으로 연관되어 있으나 한 키에서 다른 키를 계산하는
것은 현실적으로 불가능함 (키 생성 때에는 다른 정보가 사용되며, 이 정보는
키 생성 후에 바로 폐기됨)
-
공개키는 공개를 전제하며, 개인키는 그 소유주만이 알고 있음
-
문제 1: 속도가 느림
-
문제 2: 수신자의 공개키를 입수할 수 있는 신뢰성 있는 방법이 필요함
-
혼합형 암호화 알고리즘 (hybrid algorithm)
-
암호화 방법
-
E,D: 대칭 암호 알고리즘
EA,DA: 비대칭 암호 알고리즘
KU: 수신자의 공개키
KR : 수신자의 개인키
-
난수 생성기에 의해 대칭 암호키(S) 생성
-
평문 M을 대칭 암호 알고리즘으로 암호문 M'로 만든다:
-
암호키 S를 비대칭 암호 알고리즘으로 암호화:
-
M'과 S'을 함께 전달함
-
수신자의 암호 해독
-
복수의 수신자가 있는 경우, 암호화된 대칭 암호키 S'만 여러개 만들어져 함께
전달되면, 각 수신자가 자신에 맞는 키를 선택함
-
난수 생성기도 암호적 성질을 가져야 함 (예측이 불가능해야 함)
디지털 서명
-
암호학적 해쉬 함수 H의 조건
-
one-way'ness: 메시지 M 또는 해쉬값 H(M)이 주어지면 H(M') = H(M)인 메시지
M'을 찾는 일이 계산적으로 불가능해야 한다.
-
collision-resistance: H(M) = H(M')인 두 개의 서로 다른 메시지 M과 M'을
찾는 일이 계산적으로 불가능해야 한다.
-
메시지의 서명과 확인
-
서명된 메시지: M + EAKR(H(M)): KR은 발신자의 개인키로 고유성
제공
-
서명의 확인: H(M)과 DAKU(EAKR(H(M)))의 일치를 확인하며,
그 확인을 통해 서명자 인증 및 메시지가 변형이나 손상이 없었음을 검증
-
공개키 인증서(Key Certificate)의 첨부
수신자가 발신자의 공개키를 입수해 있기를 기대할 수 없는 경우, 발신자가
자신의 서명을 입증하기 위해 자신의 공개키를 공증인의 서명을 첨부하여 전달:
M + EAKR(H(M)) + KU + EACAR(KU), CAR은 공증인의 개인키로
공증인의 공개키는 쉽게 입수할 수 있는 것으로 가정함
키 관리와 키 인증 모델
-
키 분배 모델
-
개인적 키 분배
-
대칭 암호 시스템 키 센터: 각 사용자와 키 센터간의 암호 통신용 비밀키가
전달되어 있는 상황에서 사용자들사이의 암호 통신용 비밀키 분배
-
단일 공개키 서버: 소규모 조직이나 기관에 적합
-
분산 공개키 서버: 자료 중복을 허용하는 경우 자료의 일치성 유지가 중요
-
키 인증 모델
-
Web of Trust: PGP라는 소프트웨어에서 사용하는 방식으로, 누구나 자신이 확인해
줄 수 있는 사용자의 공개키에 서명을 첨부할 수 있으며, 공개키 서명 관계의
사슬을 이용해 서로 모르는 개인들 간에 키 신뢰 전이
-
Certification Authority: 공인 인증자 (개인이나 기관)
-
Certification Policy
-
분산 시스템: hierarchical 또는 general-graph
-
CRL (Certification Revocation List) 관리
전자 우편 보안 도구
| 구분 |
PEM |
S/MIME |
PGP 2.6.3 |
PGP 5.0 |
PGP 6.5.1 |
| 대칭 암호화 |
DES |
RC2
RC5
DES
3DES |
IDEA |
IDEA
3DES
CAST |
IDEA
3DES
CAST |
| 비대칭 암호화 |
RSA |
RSA |
RSA |
RSA
DH |
RSA
DH |
| 해쉬 알고리즘 |
MD2
MD5 |
MD2
MD5
SHA-1 |
MD5 |
MD5
SHA-1
RIPEMD-160 |
MD5
SHA-1
RIPEMD-160 |
| 키 인증서 |
X.509 |
X.509 |
자체 양식 |
자체 양식 |
자체 양식
X.509 |
| 기타 |
보안 규격
TIS/PEM |
보안 규격 |
freeware |
freeware
commercial |
freeware
commercial |
-
전자 우편 보안 도구들의 문제점
-
PGP: 대규모 사용자 집단에 부적합한 키 관리 방식 채택
-
PEM:엄격한 키 관리 방식의 채택으로 사용자 확보에 실패하였으며, 암호 알고리즘의
향후 추가 가능성을 열어둠으로써 구현된 소프트웨어들 사이의 호환성 확보에
문제가 될 수 있음
-
S/MIME:다양한 암호 알고리즘의 채택, 대칭 암호 알고리즘으로 수출도 가능한
RC2-40만 필수로 요구함으로써 호환성과 보안성 문제 야기
-
암호화되기 전의 평문이나 해독된 평문의 관리에 주의를 요함
-
보안 소프트웨어들간의 호환성 결여
-
전자 우편 보안 도구 사용의 위축
-
MOSS (MIME Object Security Services; PEM/MIME)의 경우 MOSS 지원 소프트웨어들사이도
호환성 없는 경우 있음
- DH in PGP is actually ElGamal Public-Key Cryptosystem:
p: a large prime, α: a primitive element in
Zp*
a: a secretly generated number in
Zp*,
β= αa mod p : public
K = (p, α, a, β) [a: private]
To encrypt a data x (usually a session key),
first generate a random number k in Zp*;
then compute eK(x,k) =
(y1, y2), where
y1 = αk mod p and
y2 = x βk mod p
Decryption can be done as follows:
dK(y1, y2) =
y2(y1a)-1
mod p = x
9.3 PGP (Pretty Good Privacy) 개요
-
PGP는 암호화와 디지탈 서명 기능을 가진 프로그램
-
개인 파일 암호화 기능
-
메시지 암호화 기능 (기밀성)
-
디지탈 서명 (인증과 무결성)
-
암호 키 관리 기능
-
1991년 Phil Zimmermann에 의해 개발된 PGP 프로그램은 전자우편과 무관하게
독립적으로 수행될 수 있으며, 명령 라인 입력 방식으로 실행하도록 만들어졌으나,
최근의 MS-Windows 용은 GUI를 갖춤
-
PGP 6.5.1의 주요 파일들 (UNIX의 경우 $HOME/.pgp에 들어감)
-
pubring.pkr
-
나 자신의 공개키와 다른 사람들의 공개키를 포함
-
암호화되어 있지 않다
-
secring.skr
-
나 자신의 비밀키(들)을 포함
-
지정된 pass phrase로부터 도출된 비밀키에 의해 대칭 암호화 알고리즘에 의해
암호화되어 있음
-
randseed.bin
-
난수 알고리즘의 seed 값을 갖고 있는 암호화된 파일
-
사용자 입력의 임의성과 대칭 암호화 알고리즘에 의해 임의성 유지
-
공개/개인 키나 세션 키 등의 발생에 이용되며, 사용된 후 매번 수정된다
-
pgp.cfg
9.4 UNIX용 PGP 6.5.1 사용법
al-linux:/home/rhee 1 > pgp -k (키 관련 명령 보기)
Pretty Good Privacy(tm) Version 6.5.1
(c) 1999 Network Associates Inc.
Uses the RSAREF(tm) Toolkit, which is copyright RSA Data Security, Inc.
Export of this software may be restricted by the U.S. government.
Key management functions:
To generate your own unique public/secret key pair:
pgp -kg
To add a key file's contents to your public, secret key ring or key server:
pgp -ka keyfile [keyring]
To remove a key or user ID from your public, secret key ring or key server:
pgp -kr userid [keyring | URL]
To edit your user ID or pass phrase:
pgp -ke your_userid [keyring]
To extract (copy) a key from your public or secret key ring:
pgp -kx userid keyfile [keyring | URL]
To view the contents of your public key ring or query the keyserver:
pgp -kv[v] [userid] [keyring | URL]
To check signatures on your public key ring:
pgp -kc [userid] [keyring]
To sign someone else's public key on your public key ring:
pgp -ks her_userid [-u your_userid] [keyring]
To remove selected signatures from a userid on a keyring or key server:
pgp -krs userid [keyring]
al-linux:/home/rhee 2 > pgp -kg (키의 생성)
Pretty Good Privacy(tm) Version 6.5.1
(c) 1999 Network Associates Inc.
Uses the RSAREF(tm) Toolkit, which is copyright RSA Data Security, Inc.
Export of this software may be restricted by the U.S. government.
Choose the public-key algorithm to use with your new key
1) DSS/DH (a.k.a. DSA/ElGamal) (default)
2) RSA
Choose 1 or 2: 1
Choose the type of key you want to generate
1) Generate a new signing key (default)
2) Generate an encryption key for an existing signing key
Choose 1 or 2: 1
Pick your DSS ``master key'' size:
1) 1024 bits- Maximum size (Recommended)
Choose 1 or enter desired number of bits: 1
Generating a 1024-bit DSS key.
You need a user ID for your public key. The desired form for this
user ID is your name, followed by your E-mail address enclosed in
<angle brackets>, if you have an E-mail address.
For example: John Q. Smith <jqsmith@nai.com>
Enter a user ID for your public key: Gwangsoo Rhee <rhee@al-linux.sookmyung.ac.kr>
Enter the validity period of your signing key in days from 0 - 10950
0 is forever (the default is 0): 30
You need a pass phrase to protect your DSS secret key.
Your pass phrase can be any sentence or phrase and may have many
words, spaces, punctuation, or any other printable characters.
Enter pass phrase:
Enter same pass phrase again:
PGP will generate a signing key. Do you also require an
encryption key? (Y/n)
Pick your DH key size:
1) 1024 bits- High commercial grade, secure for many years
2) 2048 bits- "Military" grade, secure for forseeable future
3) 3072 bits- Archival grade, slow, highest security
Choose 1, 2, 3, or enter desired number of bits: 1
Enter the validity period of your encryption key in days from 0 - 30
0 is forever (the default is 30):
Note that key generation is a lengthy process.
PGP needs to generate some random data. This is done by measuring
the time intervals between your keystrokes. Please enter some
random text on your keyboard until the indicator reaches 100%.
Press ^D to cancel
Enough, thank you.
....******* ..........******* .
Make this the default signing key? (Y/n)
..................******* ....*******
Key generation completed.
al-linux:/home/rhee 3 > ls -al .pgp
total 12
drwx------ 2 rhee staff 1024 Aug 17 17:08 ./
drwx------ 5 rhee staff 1024 Aug 17 17:06 ../
-rw------- 1 rhee staff 2117 Aug 17 17:06 PGPMacBinaryMappings.txt
-rw------- 1 rhee staff 146 Aug 17 16:22 PGPgroup.pgr
-rw------- 1 rhee staff 171 Aug 17 17:08 PGPsdkPreferences
-rw------- 1 rhee staff 0 Aug 17 16:22 pgp.cfg
-rw------- 1 rhee staff 0 Aug 17 16:22 pubring-bak-1.pkr
-rw------- 1 rhee staff 921 Aug 17 17:08 pubring-bak-2.pkr
-rw------- 1 rhee staff 921 Aug 17 17:08 pubring.pkr
-rw------- 1 rhee staff 512 Aug 17 17:08 randseed.rnd
-rw------- 1 rhee staff 0 Aug 17 16:22 secring-bak-1.skr
-rw------- 1 rhee staff 1007 Aug 17 17:08 secring-bak-2.skr
-rw------- 1 rhee staff 1007 Aug 17 17:08 secring.skr
al-linux:/home/rhee 4 > pgp -kx rhee rhee.asc (키의 추출)
Pretty Good Privacy(tm) Version 6.5.1
(c) 1999 Network Associates Inc.
Uses the RSAREF(tm) Toolkit, which is copyright RSA Data Security, Inc.
Export of this software may be restricted by the U.S. government.
Extracting from keyring '/home/rhee/.pgp/pubring.pkr', userid "rhee".
Key extracted to file 'rhee.asc'.
al-linux:/home/rhee 5 > cat rhee.asc
-----BEGIN PGP PUBLIC KEY BLOCK-----
Version: PGP 6.5.1
mQGiBDe5GGARBADeC8JY9mXVR6d4B5lpwyWxZ4/Dpcoqlcd6B/Za73K2xHz6+YMO
QwbySyn/IooYPmdJvp60W3rHjQeRjiEPeriAEDYvgzmF1w9jUdhCjQtKBwUvW91v
jc7Qbbbrg3MgFBCFbQhV3vWjZhCxynfH/hMqDafW/79KeZ3wdpuI/DcUTwCg//sS
bJRDR4+H8v/VMksXxM2k8HMEAMvklegiL/oPQbOvuPy2f3epNonC8Al8BehiM6Pu
MO3NtBFKN0v9qu5M+OZDP0aj0OA1Aj0H7LsVWm2MLgpr7F7XSmMy4/XW8lTJwkOr
aWPxeeplykO6cmvP4CLUoMn1EZWxN25gSPttT0425BJSsagRDlJO6amc9fgiZxr7
3/sBA/4k8ItwcT2IrqlnN4UjMueCJlvRiF3JXws8mWJ5PKMDTc6RMODuTinLic4P
h71SKoTVyA2Vn9AETTeukZVtEAAPjHBvuWJ2RfiSQH8YBGMnefxAGWHLxqTnxLS9
Y/gX4s7Ji7NdrzDSmur1yVtWQDIz60bqVMMVs55P6c6XXFkoILQtR3dhbmdzb28g
UmhlZSA8cmhlZUBhbC1saW51eC5zb29rbXl1bmcuYWMua3I+iQBUBBARAgAUBQI3
uRhgBQkAJ40ABAsDAQICGQEACgkQyQgv6gqcSpGGZQCg4r2XDPIu2wBDSRdL14yj
7VoR16UAn1i+Gte6GCnzN7AI+6pHQ/VDmc9LuQENBDe5GGcQBADDj1x4YSxALFiS
4duUZbfCcX2ebIpnIJOE5chvgwo78GqEXh12BJCW46RFh1wx8GXyJUfZfrQT9eVW
0KsK74s+K1DXutJB/J+IrfRPUggOp86Jq8xxhE5LGalqeR/b6MXrjY6OmwafpS3B
pzyuueiie16V2zAG+Fa7X8R2oR7JwwACAgP/XL+BdLCEm6oCbEFJ8Txxypfh8t+4
gm+Nc3oF0eJCP5WtdWx7onElCh4jxzHQLsrSpTiklM7U9X+QVeCcUhNsSTXimZXi
BbDCuyqqHolpi8gYlYuiagqPB88t3sFf7puRRZUxLM90UMQNzrZYijOnd6RP4GVJ
DN6pYXi0Y1qWrs6JAEwEGBECAAwFAje5GGcFCQAnjQAACgkQyQgv6gqcSpE+NQCf
SORBhbEu2S+u3XyxuB3evan2urgAn0GC/i8DjRy8Qv2lOgsjN1Z8G1BK
=wFqS
-----END PGP PUBLIC KEY BLOCK-----
al-linux:/home/rhee 6 > Mail
Mail version 8.1 6/6/93. Type ? for help.
"/var/spool/mail/rhee": 2 messages 1 new
1 MAILER-DAEMON@al-lin Sat Jul 31 18:29 12/523 "DON'T DELETE THIS MES"
>N 2 dummy1@al-linux.sook Sat Aug 21 16:23 36/1712 "PGP Key from Dummy 1"
& 2
Message 2:
From dummy1 Sat Aug 21 16:23:47 1999
Date: Sat, 21 Aug 1999 16:23:47 +0900
From: Dummy 1 <dummy1@al-linux.sookmyung.ac.kr>
To: rhee@al-linux.sookmyung.ac.kr
Subject: PGP Key from Dummy 1
-----BEGIN PGP PUBLIC KEY BLOCK-----
Version: PGP 6.5.1
mQGiBDeliWgRBADq0P5VyiqjMx5CGBCdtDeBZDjV2BbUVJZCrvBmARdIuwr6A1/r
rjZ+I8vZ7w5Gf1S9clT4JvAY/EMwpt9mqojswLsg2IhyCzp4+AljChb+x5jwXHYX
LrLJjK3FsJ/7S+pJzx1saJd192qwJNtCzhLoiQuzmdGt7K8gtSUIKGRKvQCg/7qJ
zhwemqFIKr2GHrSSsMIUyAkEAJAuGYJ33lSyOI7Euq+avSmoV+3AiiAaALE3kXgW
MumcG7+J3EJNtIZNNbPfH0rouJZMHLJwfORLoJgm0Td+rYX+SoOo5JSmG9+vIKmu
IHPJOqb+VOEhVBAya5B5b5Zp2xd2bIqXkEIxsqC2apOYWB+FE+lFT1bzisnmxsSk
Jw6qA/98FP0GyCmh2rz9nOwu6p9Hp0BWsjmeHUKRcv2EtB+9EqRWvbr/yMk5Ac5E
/edJO897UZ14dT1/oURLznsNfSXh2YFl7ODUAvazG1o99HEkxPjQs9Rml870I6Ku
13vRr5nPBUUOK9w4ccgXyXU2PdB7hYVDrV3r0AQND4LffyVNArQpRHVtbXkgMSA8
ZHVtbXkxQGFsLWxpbnV4LnNvb2tteXVuZy5hYy5rcj6JAE4EEBECAA4FAjeliWgE
CwMBAgIZAQAKCRChjLBZl3O7eHWaAKC0B4U3AxYfVWpsB/w+OyRPoEx4xACgnNAu
a78gf95aBrJB1e8mnEnUXTa5AQ0EN6WJbxAEAPJRkXFc+SEpW+Ai/4ATO3j4z0Em
�o0n3aeim9T2srwt/UtCIe0l7EsGREOpSqPuxKAX/NWjiIkEkwAm5NX9aiaq8MYWf
hlJ22IZLsnRAgeXK39s6Z4Xf8oTHgJnh2YEv761j2dIlVjZycsZ7DaroGnlQnsB+
94SdlSyO/J2ozDN9AAICA/9gPqmMGXK3zsWUMLwCB8mdA73V1xSODPFjXV4fVIBB
NcbqjjsXhHxDHGh1u1UCee3jxsWpXDeioJRCCLdqTk+PlTtnNoGoaKRpLLmPtq70
uQly7NjMf7IupCNVX5DuS/PaNha4ooe4wVZNAM664Mddno4UY8jPVxteHEcb6Or2
zYkARgQYEQIABgUCN6WJbwAKCRChjLBZl3O7eJ/iAKCr3D35ceiuCQJmLQFZFixO
G7nbXQCePKf21xyuMdKHTjx+ouCW5HaE7gI=
=QlaB
-----END PGP PUBLIC KEY BLOCK-----
& w 2 dummy.asc
"dummy.asc" [New file]
& x
al-linux:/home/rhee 7 > cat dummy.asc
-----BEGIN PGP PUBLIC KEY BLOCK-----
Version: PGP 6.5.1
mQGiBDeliWgRBADq0P5VyiqjMx5CGBCdtDeBZDjV2BbUVJZCrvBmARdIuwr6A1/r
rjZ+I8vZ7w5Gf1S9clT4JvAY/EMwpt9mqojswLsg2IhyCzp4+AljChb+x5jwXHYX
LrLJjK3FsJ/7S+pJzx1saJd192qwJNtCzhLoiQuzmdGt7K8gtSUIKGRKvQCg/7qJ
zhwemqFIKr2GHrSSsMIUyAkEAJAuGYJ33lSyOI7Euq+avSmoV+3AiiAaALE3kXgW
MumcG7+J3EJNtIZNNbPfH0rouJZMHLJwfORLoJgm0Td+rYX+SoOo5JSmG9+vIKmu
IHPJOqb+VOEhVBAya5B5b5Zp2xd2bIqXkEIxsqC2apOYWB+FE+lFT1bzisnmxsSk
Jw6qA/98FP0GyCmh2rz9nOwu6p9Hp0BWsjmeHUKRcv2EtB+9EqRWvbr/yMk5Ac5E
/edJO897UZ14dT1/oURLznsNfSXh2YFl7ODUAvazG1o99HEkxPjQs9Rml870I6Ku
13vRr5nPBUUOK9w4ccgXyXU2PdB7hYVDrV3r0AQND4LffyVNArQpRHVtbXkgMSA8
ZHVtbXkxQGFsLWxpbnV4LnNvb2tteXVuZy5hYy5rcj6JAE4EEBECAA4FAjeliWgE
CwMBAgIZAQAKCRChjLBZl3O7eHWaAKC0B4U3AxYfVWpsB/w+OyRPoEx4xACgnNAu
a78gf95aBrJB1e8mnEnUXTa5AQ0EN6WJbxAEAPJRkXFc+SEpW+Ai/4ATO3j4z0Em
o0n3aeim9T2srwt/UtCIe0l7EsGREOpSqPuxKAX/NWjiIkEkwAm5NX9aiaq8MYWf
hlJ22IZLsnRAgeXK39s6Z4Xf8oTHgJnh2YEv761j2dIlVjZycsZ7DaroGnlQnsB+
94SdlSyO/J2ozDN9AAICA/9gPqmMGXK3zsWUMLwCB8mdA73V1xSODPFjXV4fVIBB
NcbqjjsXhHxDHGh1u1UCee3jxsWpXDeioJRCCLdqTk+PlTtnNoGoaKRpLLmPtq70
uQly7NjMf7IupCNVX5DuS/PaNha4ooe4wVZNAM664Mddno4UY8jPVxteHEcb6Or2
zYkARgQYEQIABgUCN6WJbwAKCRChjLBZl3O7eJ/iAKCr3D35ceiuCQJmLQFZFixO
G7nbXQCePKf21xyuMdKHTjx+ouCW5HaE7gI=
=QlaB
-----END PGP PUBLIC KEY BLOCK-----
al-linux:/home/rhee 8 > pgp -kv (키 보기)
Pretty Good Privacy(tm) Version 6.5.1
(c) 1999 Network Associates Inc.
Uses the RSAREF(tm) Toolkit, which is copyright RSA Data Security, Inc.
Export of this software may be restricted by the U.S. government.
Type bits keyID Date User ID
DSS 1024/1024 0x0A9C4A91 1999/08/17 expires 1999/09/16
*** DEFAULT SIGNING KEY ***
Gwangsoo Rhee <rhee@al-linux.sookmyung.ac.kr>
1 matching key found.
al-linux:/home/rhee 9 > pgp -kvv (키 자세히 보기)
Pretty Good Privacy(tm) Version 6.5.1
(c) 1999 Network Associates Inc.
Uses the RSAREF(tm) Toolkit, which is copyright RSA Data Security, Inc.
Export of this software may be restricted by the U.S. government.
Type bits keyID Date User ID
DSS 1024 0x0A9C4A91 1999/08/17 expires 1999/09/16
DH 1024 0x0A9C4A91 1999/08/17 expires 1999/09/16
*** DEFAULT SIGNING KEY ***
Gwangsoo Rhee <rhee@al-linux.sookmyung.ac.kr>
sig 0x0A9C4A91 Gwangsoo Rhee <rhee@al-linux.sookmyung.ac.kr>
1 matching key found.
al-linux:/home/rhee 10 > pgp -ka dummy.asc (키의 추가)
Pretty Good Privacy(tm) Version 6.5.1
(c) 1999 Network Associates Inc.
Uses the RSAREF(tm) Toolkit, which is copyright RSA Data Security, Inc.
Export of this software may be restricted by the U.S. government.
Looking for new keys...
DSS 1024/1024 0x9773BB78 1999/08/02 Dummy 1 <dummy1@al-linux.sookmyung.ac.kr>
sig? 0x9773BB78 (Unknown signator, can't be checked)
keyfile contains 1 new keys. Add these keys to keyring ''? (Y/n)
Keyfile contains:
1 new key(s)
al-linux:/home/rhee 11 > pgp -kvv
Pretty Good Privacy(tm) Version 6.5.1
(c) 1999 Network Associates Inc.
Uses the RSAREF(tm) Toolkit, which is copyright RSA Data Security, Inc.
Export of this software may be restricted by the U.S. government.
Type bits keyID Date User ID
DSS 1024 0x9773BB78 1999/08/02
DH 1024 0x9773BB78 1999/08/02 Dummy 1 <dummy1@al-linux.sookmyung.ac.kr>
sig 0x9773BB78 Dummy 1 <dummy1@al-linux.sookmyung.ac.kr>
DSS 1024 0x0A9C4A91 1999/08/17 expires 1999/09/16
DH 1024 0x0A9C4A91 1999/08/17 expires 1999/09/16
*** DEFAULT SIGNING KEY ***
Gwangsoo Rhee <rhee@al-linux.sookmyung.ac.kr>
sig 0x0A9C4A91 Gwangsoo Rhee <rhee@al-linux.sookmyung.ac.kr>
2 matching keys found.
al-linux:/home/rhee 12 > cat sample
alias gcc 'gcc -ansi -O0'
alias h history
alias help man
alias df 'df -k'
alias lo logout
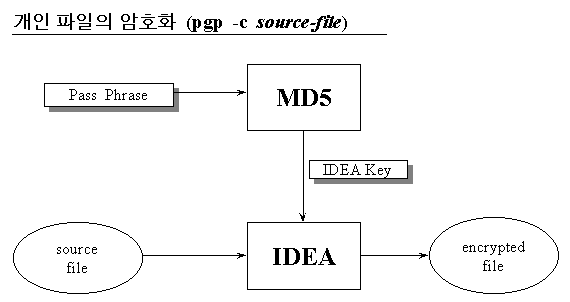
al-linux:/home/rhee 13 > pgp -c sample (개인 파일의 암호화)
Pretty Good Privacy(tm) Version 6.5.1
(c) 1999 Network Associates Inc.
Uses the RSAREF(tm) Toolkit, which is copyright RSA Data Security, Inc.
Export of this software may be restricted by the U.S. government.
You need a pass phrase to encrypt the file.
Enter pass phrase:
Enter same pass phrase again:
Ciphertext file: sample.pgp
al-linux:/home/rhee 14 > pgp -ca sample (개인 파일의 암호화, ASCII 출력)
Pretty Good Privacy(tm) Version 6.5.1
(c) 1999 Network Associates Inc.
Uses the RSAREF(tm) Toolkit, which is copyright RSA Data Security, Inc.
Export of this software may be restricted by the U.S. government.
You need a pass phrase to encrypt the file.
Enter pass phrase:
Enter same pass phrase again:
Transport armor file: sample.asc
al-linux:/home/rhee 15 > ls -l sample*
-rw-r--r-- 1 rhee staff 103 Aug 21 16:32 sample
-rw------- 1 rhee staff 219 Aug 21 16:34 sample.asc
-rw------- 1 rhee staff 101 Aug 21 16:33 sample.pgp
al-linux:/home/rhee 16 > cat sample.asc
-----BEGIN PGP MESSAGE-----
Version: PGP 6.5.1
pGNMhPgqZCT1WDlcoSbS5tgiJxZY3Mj0r+xkBskKif54SeqlGp3N29f8tT+UdNoh
oyX5OTHUK+xs0vyrzSOCc2HWoJpuE1xOESvtBXfC4VQO0qOzdRHLYMuodn4YEWYM
ti6oQ5M=
=+mDT
-----END PGP MESSAGE-----
al-linux:/home/rhee 17 > rm sample
al-linux:/home/rhee 18 > pgp sample.pgp (암호화된 파일 보기: 해독 및 서명 확인)
Pretty Good Privacy(tm) Version 6.5.1
(c) 1999 Network Associates Inc.
Uses the RSAREF(tm) Toolkit, which is copyright RSA Data Security, Inc.
Export of this software may be restricted by the U.S. government.
File is encrypted. You need a pass phrase to decrypt this file.
Enter pass phrase:
Plaintext filename: sample
al-linux:/home/rhee 19 > cat sample
alias gcc 'gcc -ansi -O0'
alias h history
alias help man
alias df 'df -k'
alias lo logout
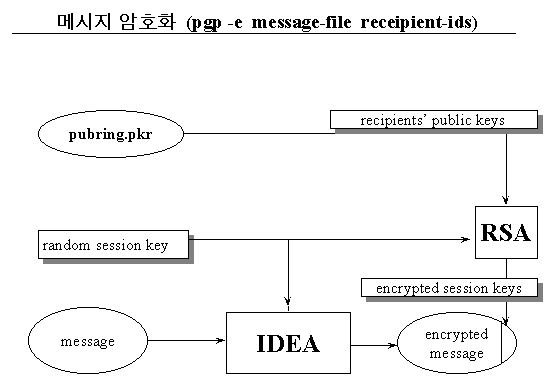
al-linux:/home/rhee 20 > pgp -e sample rhee dummy1 (rhee와 dummy1에게 보낼 파일을 암호화)
Pretty Good Privacy(tm) Version 6.5.1
(c) 1999 Network Associates Inc.
Uses the RSAREF(tm) Toolkit, which is copyright RSA Data Security, Inc.
Export of this software may be restricted by the U.S. government.
Recipients' public key(s) will be used to encrypt.
Key for user ID: Gwangsoo Rhee <rhee@al-linux.sookmyung.ac.kr>
1024-bit DSS key, Key ID 0x0A9C4A91, created 1999/08/17, expires 1999/09/16
Key can sign.
Key for user ID: Dummy 1 <dummy1@al-linux.sookmyung.ac.kr>
1024-bit DSS key, Key ID 0x9773BB78, created 1999/08/02
WARNING: Because this public key is not certified with a trusted
signature, it is not known with high confidence that this public key
actually belongs to: "Dummy 1 <dummy1@al-linux.sookmyung.ac.kr>".
Are you sure you want to use this public key (y/N)? y
�Output file 'sample.pgp' already exists. Overwrite (y/N)? y
Ciphertext file: sample.pgp
al-linux:/home/rhee 21 > ls -l sample*
-rw------- 1 rhee staff 103 Aug 21 16:35 sample
-rw------- 1 rhee staff 219 Aug 21 16:34 sample.asc
-rw------- 1 rhee staff 653 Aug 21 16:39 sample.pgp
al-linux:/home/rhee 22 > pgp sample.pgp
Pretty Good Privacy(tm) Version 6.5.1
(c) 1999 Network Associates Inc.
Uses the RSAREF(tm) Toolkit, which is copyright RSA Data Security, Inc.
Export of this software may be restricted by the U.S. government.
File is encrypted. Secret key is required to read it.
Key for user ID: Gwangsoo Rhee <rhee@al-linux.sookmyung.ac.kr>
1024-bit DSS key, Key ID 0x0A9C4A91, created 1999/08/17, expires 1999/09/16
Key can sign.
You need a pass phrase to unlock your secret key.
Enter pass phrase:
Output file 'sample' already exists. Overwrite (y/N)? N
Enter new file name: sample1
Plaintext filename: sample1
al-linux:/home/rhee 23 > cat sample1
alias gcc 'gcc -ansi -O0'
alias h history
alias help man
alias df 'df -k'
alias lo logout
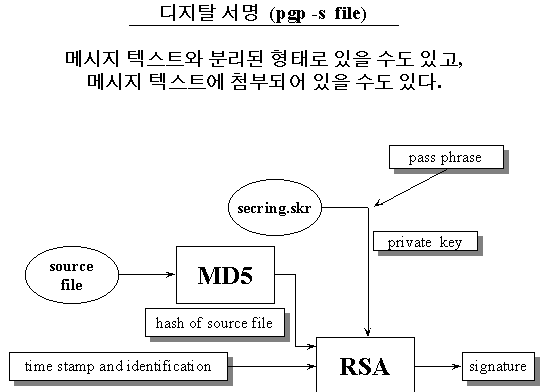
al-linux:/home/rhee 24 > pgp -s sample (메시지 서명)
Pretty Good Privacy(tm) Version 6.5.1
(c) 1999 Network Associates Inc.
Uses the RSAREF(tm) Toolkit, which is copyright RSA Data Security, Inc.
Export of this software may be restricted by the U.S. government.
A secret key is required to make a signature.
You need a pass phrase to unlock your secret key.
Key for user ID "Gwangsoo Rhee <rhee@al-linux.sookmyung.ac.kr>"
Enter pass phrase:
Passphrase is good
Output file 'sample.pgp' already exists. Overwrite (y/N)? y
Signature file: sample.pgp
al-linux:/home/rhee 25 > ls -l sample*
-rw------- 1 rhee staff 103 Aug 21 16:35 sample
-rw------- 1 rhee staff 219 Aug 21 16:34 sample.asc
-rw------- 1 rhee staff 157 Aug 21 16:41 sample.pgp
-rw------- 1 rhee staff 103 Aug 21 16:40 sample1
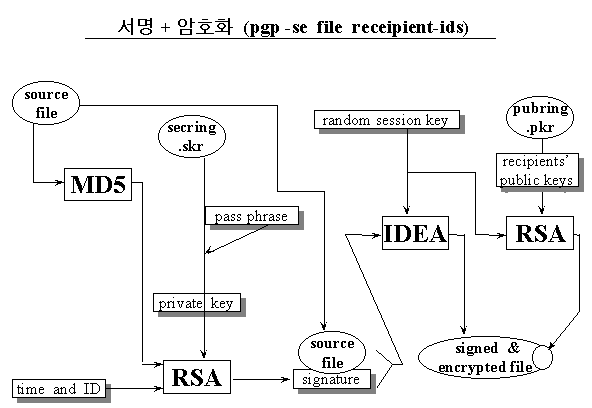
al-linux:/home/rhee 26 > pgp -esa sample dummy1 (sample이라는
파일을 dummy1이 읽을 수 있도록 암호화하면서, rhee가 서명)
Pretty Good Privacy(tm) Version 6.5.1
(c) 1999 Network Associates Inc.
Uses the RSAREF(tm) Toolkit, which is copyright RSA Data Security, Inc.
Export of this software may be restricted by the U.S. government.
A secret key is required to make a signature.
Recipients' public key(s) will be used to encrypt.
You need a pass phrase to unlock your secret key.
Key for user ID "Gwangsoo Rhee <rhee@al-linux.sookmyung.ac.kr>"
Enter pass phrase:
Passphrase is good
Key for user ID: Dummy 1 <dummy1@al-linux.sookmyung.ac.kr>
1024-bit DSS key, Key ID 0x9773BB78, created 1999/08/02
WARNING: Because this public key is not certified with a trusted
signature, it is not known with high confidence that this public key
actually belongs to: "Dummy 1 <dummy1@al-linux.sookmyung.ac.kr>".
Are you sure you want to use this public key (y/N)?y
�Output file 'sample.asc' already exists. Overwrite (y/N)? y
Transport armor file: sample.asc
al-linux:/home/rhee 27 > ls -l sample*
-rw------- 1 rhee staff 103 Aug 21 16:35 sample
-rw------- 1 rhee staff 702 Aug 21 16:42 sample.asc
-rw------- 1 rhee staff 157 Aug 21 16:41 sample.pgp
-rw------- 1 rhee staff 103 Aug 21 16:40 sample1
al-linux:/home/rhee 28 > cat sample.asc
-----BEGIN PGP MESSAGE-----
Version: PGP 6.5.1
qANQR1DBwE4DJZXL/so79NMQA/9QjYTos3fY1/VMybyuh6AOJWwprutwm7+hwLyW
N8Twgatod8eUREgFul04FakuOhIe+RC5+/cxHsxqBABE3lXY12AGTLl40Vaz0Fw0
/pNQkK0b9vS7x6EUDkNMWXTdlDY1hBTBuBWcqZMpAiFsfYxs5OSLZeDbyncrzVEy
U9L5sgP/dPFASLgGbsOoWxRyZpdg+tzxQnt6UaKT0HfX2FwZFzNs5GfEDf6KdoZ2
89MIDkj983i3IyLqc3HEJ/Lq2hJOJHevyqAwYZS0Pobv6idoQSA2IYLvmLasITog
VtXWOGSQVAprMaHNTS+8qE03MYluMorPu4G+rDykYgWFDiqzce7JsqoWn7Rg0ZNR
csW9jPqI6rN6sh9MfNHIe2sCX4mMEegFljVydb2ti2W+YPuc59nKjl6jUqS7ZjRn
fIHVzVYsGK+pjsxr2upy/de4IfLlViwemRP3OY8aIW4DP+uqLkCTMjy8nMYreqh7
6jiAj5SlizSEqtBXfyokqTKSgiipKnAJL4GODL5CBOgk+CO+wBTVvq/w+tVkAXEv
4ifyCBvoqdL6gedNrTZs9Z9Inscpaq0D7t0=
=c9bj
-----END PGP MESSAGE-----
al-linux:/home/rhee 29 > Mail -s "Signed and Encrypted" dummy1 < sample.asc
al-linux:/home/rhee 27 > telnet al-linux
Trying 203.252.195.104...
Connected to al-linux.sookmyung.ac.kr.
Escape character is '^]'.
ALzzA Linux release 5.2 (PatchMan Dreams of World Domination)
Kernel 2.0.36 on an i686
login: dummy1
Password:
Last login: Sat Aug 21 16:20:42 from al-linux
You have new mail.
al-linux:/home/user/dummy1 1 > Mail
Mail version 8.1 6/6/93. Type ? for help.
"/var/spool/mail/dummy1": 2 messages 2 new
>N 1 rhee@al-linux.sookmy Sat Aug 21 16:33 35/1704 "Rhee's Public Key"
N 2 rhee@al-linux.sookmy Sat Aug 21 16:44 27/1129 "Signed and Encrypted"
& w 1 rhee.asc
"rhee.asc" [New file]& w 2 m.asc
& w 2 m.asc
"m.asc" [New file]
& x
al-linux:/home/user/dummy1 2 > pgp -kvv
Pretty Good Privacy(tm) Version 6.5.1
(c) 1999 Network Associates Inc.
Uses the RSAREF(tm) Toolkit, which is copyright RSA Data Security, Inc.
Export of this software may be restricted by the U.S. government.
Type bits keyID Date User ID
DSS 1024 0x9773BB78 1999/08/02
DH 1024 0x9773BB78 1999/08/02 *** DEFAULT SIGNING KEY ***
Dummy 1 <dummy1@al-linux.sookmyung.ac.kr>
sig 0x9773BB78 Dummy 1 <dummy1@al-linux.sookmyung.ac.kr>
1 matching key found.
al-linux:/home/user/dummy1 3 > pgp -ka rhee.asc
Pretty Good Privacy(tm) Version 6.5.1
(c) 1999 Network Associates Inc.
Uses the RSAREF(tm) Toolkit, which is copyright RSA Data Security, Inc.
Export of this software may be restricted by the U.S. government.
Looking for new keys...
DSS 1024/1024 0x0A9C4A91 1999/08/17 Gwangsoo Rhee <rhee@al-linux.sookmyung.ac.kr>
sig? 0x0A9C4A91 (Unknown signator, can't be checked)
keyfile contains 1 new keys. Add these keys to keyring ''? (Y/n)
Keyfile contains:
1 new key(s)
al-linux:/home/user/dummy1 4 > pgp m.asc
Pretty Good Privacy(tm) Version 6.5.1
(c) 1999 Network Associates Inc.
Uses the RSAREF(tm) Toolkit, which is copyright RSA Data Security, Inc.
Export of this software may be restricted by the U.S. government.
File is encrypted. Secret key is required to read it.
Key for user ID: Dummy 1 <dummy1@al-linux.sookmyung.ac.kr>
1024-bit DSS key, Key ID 0x9773BB78, created 1999/08/02
Key can sign.
You need a pass phrase to unlock your secret key.
Enter pass phrase:
Good signature from user "Gwangsoo Rhee <rhee@al-linux.sookmyung.ac.kr>".
Signature made 1999/08/21 07:43 GMT
WARNING: Because this public key is not certified with a trusted
signature, it is not known with high confidence that this public key
actually belongs to: "Gwangsoo Rhee <rhee@al-linux.sookmyung.ac.kr>".
Plaintext filename: m
-
PGP의 주요 기능과 내부 작동 원리
-
UNIX Mail에서의 사용 방법
-
보낼 때: pgp -esaf file recipients | Mailrecipient-address
-
읽을 때: (Mail 안에서)
pipe 메시지 번호
pgp [but,
not in Linux]
-
UNIX elm이나 MS-Windows용인 Eudora 등에서는 mailer안에서 PGP 처리 가능
-
키의 생성, 키의 export/import, 키에 대한 서명 (신뢰의 설정) 등의 사전 작업
필요
-
Windows 용에서는 online key server 설정하여 사용 (ldap://cs.sookmyung.ac.kr:389/)
-
PGP 사용시에 고려되어야 할 사항들
-
공개키의 분배
- key fingerprint: hash output of the key (pgp -kvc)
-
평문의 생성과 보존
-
평문을 UNIX에서 편집기로 생성할 경우 /tmp 디렉토리에 노출
-
UNIX 호스트 콘솔이외에서 작업할 경우 패킷 스니핑 공격에 노출
-
암호문을 만든 후 평문 파일을 지우더라도 파일의 내용에 대한 흔적이 남게
되며, 그 흔적조차 지우는 유틸리티 사용이 요구됨
- -m flag (more): for your eyes only; can be used both in encryption
and in decryption
- -w flag (more): wipe out the plaintext after encrypting;
overwrites the file 26 times
-
수신자측에서도 위의 세가지 위협이 동일하게 적용됨
9.5 기타 전자 우편 보안 관련 사항들
MIME 보안
-
MIME 메시지의 내용은 그 자체로 프로그램이거나 다른 프로그램의 데이타이며,
자동 수행 방식으로 읽혀지면 보안 문제를 일으킬 수 있다.
-
MIME 데이타를 암호화해버리면 원래 데이타의 헤더 등에 들어 있는 제어 정보등이
감추어져 있어 기존의 MIME 메일 프로그램에서 처리하기 곤란하다.
-
메시지에 첨부된 디지털 서명이나 키 인증서, 사용된 암호 알고리즘이나 관련
정보 등을 MIME형식으로 첨부하면 체계적으로 처리할 수 있다.
-
MIME 보안을 위한 제안들
-
PGP/MIME (RFC 2015; 1996년 10월)
-
MOSS (RFC 1848; 1995년 10월)
-
S/MIME (RSA사 --> IETF 표준화 진행 중)
-
Netscape나 IE 등에서 사용 가능
-
Key Certificate 신청
-
키의 전달은 서명된 메시지의 전달로 이루어짐
-
암호화 및 서명 기능이 있음
발신자 부인 방지(Sender Non-repudiation)
-
신뢰성 및 법적 효력 있는 키 관리 필요
-
메시지와 디지털 서명의 보존을 요함
메시지 수신 사실 및 내용 확인 통보
-
S/MIME에서 확장 기능으로 검토 중 (S/MIME Confirm)
-
S/MIME Client를 쓰지 않거나 관련 기능을 우회하는 것이 가능함
발신 사실이나 내용 증명
-
공신력 있는 제 3자의 개입을 필요로 함
-
S/MIME에서 확장 기능으로 검토 중 (S/MIME 3P)
Traffic-flow 기밀성
-
발신자/수신자간 메시지 전송 사실이나 전송 빈도, 메시지 크기 등을 숨김
-
메시자와 암호화된 수신자 주소를 받아 재전송해주는 remailer 사용
-
가짜 메시지를 생성/소멸하거나 메시지 크기를 일정하게 유지하기 위한 padding의
사용
발신자 익명성
-
수신자로부터 발신자의 신분을 감춤
-
remailer를 사용하되 보안성 강화를 위해 다수의 remailer 사용이 바람직함
-
remailers R1, R2, ..., Rn-1과 최종 수신자
Rn의 공개키를 KUi(i=1,...,n)라면, R1은
EAKU1(R2 + EAKU2(R3 + EAKU3(...
+ EAKUn-1(Rn)...))) + EAKUn(M)를, R2는
EAKU2(R3 + EAKU3(R4 + EAKU4(...
+ EAKUn-1(Rn)...))) + EAKUn(M)를, ...,
Rn은 EAKUn(M)을 받게 되며, 각 remailer Ri는
Ri-1과 Ri+1이외에 대한 정보를 알 수 없게 된다.
Spam (junk e-mail)
-
광고/홍보 등을 목적으로 다수의 사용자에게 보내지는 전자 우편
-
전자 우편 주소는 뉴스 그룹이나 우편링 리스트, WWW, Anonymous FTP, 개별적인
전자 우편 패킷 스니핑 등으로 자동 추출에 의해 수집
-
방어
-
자신의 전자 우편 주소가 xxx@yyy.zzz라면, xx^x@yy^y.zzz와 같이 특수 문자를
끼워 넣어주고 그러한 사실을 알려주는 문구를 메시지로 첨부해주는 filter를
사용: 자동 추출에 대한 미약한 방어
-
spam 광고물은 전문적으로 위탁 처리되는 경우가 많으므로, 알려진 spam 생성지로부터의
메시지를 제거해주는 filter를 사용: 사용자 수준이나, 호스트 수준, 또는 Mail
게이트웨이 수준에서 설치 가능
전자 우편 바이러스
-
interpret되는 명령을 포함하는 메시지로 워드나 포스트스크립트 텍스트
-
발신자에 대한 인증의 사용으로 일부 방어 가능



